Phishing tops the list of data privacy and security risks concerns for most organizations according to a survey completed by Deloitte leaders. And, these concerns are valid. Email users continue to be overconfident about their ability to spot phishing messages. What’s worse is that users believe that their Antispam protection in Microsoft Outlook will protect them. The reality is that there is no foolproof method of blocking 100% of threats.
What Is Phishing?
Phishing is one of the many methods used by cybercriminals to gain sensitive data from users. Individuals are targeted via email, telephone or text message by someone posing as a legitimate institution to lure them into providing passwords, company information, credit card info and more.

How Can I Protect My Company?
Education is the key to preventing breaches. Since 91% of data breaches begin with a phishing email, it is vital employees understand how to spot them.
What Does A Phishing Email Look Like?
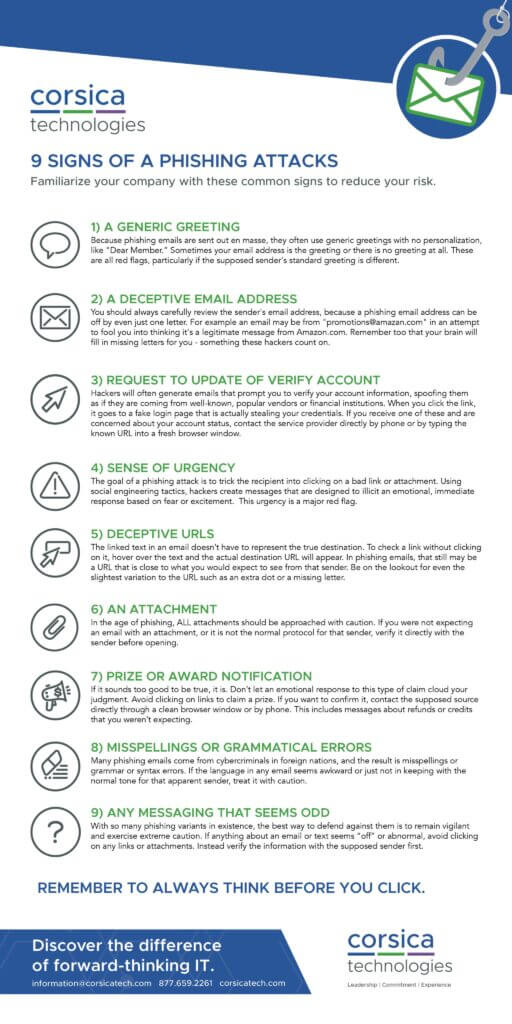
Phishing emails come in many variations, but there are some common red flags to look for to help identify suspicious emails. Check out our infographic below of the 9 Common Signs of a Phishing Attack. When your employees or end-users are aware of these red flags, your data will be much safer from a disaster like a phishing scam.
Download Our Red Flag Phishing Infographic Now
Don’t wait for a Cyber Attack. Plan and Prepare for it.
While awareness and security education aren’t 100% foolproof, they are a crucial tool for success when working to achieve the level of information security you need for your business in today’s world. Corsica offers phishing training and security awareness training that will drastically reduce your employees phish prone percentage. In fact, we’re offering a Free Phishing Test to organizations to test the knowledge of their team. Included in the test is results review to understand how you can take action.
Cyber criminals are constantly developing new techniques to attack your organization. Cybersecurity is a process of continuous improvement, not a destination at which your organization suddenly arrives. As cyber threats continue to evolve, so must your cybersecurity strategy.
If you would like some help moving your organization forward on the cybersecurity front or more information about the solutions discussed above give us a call at (855) 411-3387or reach out to us here.






